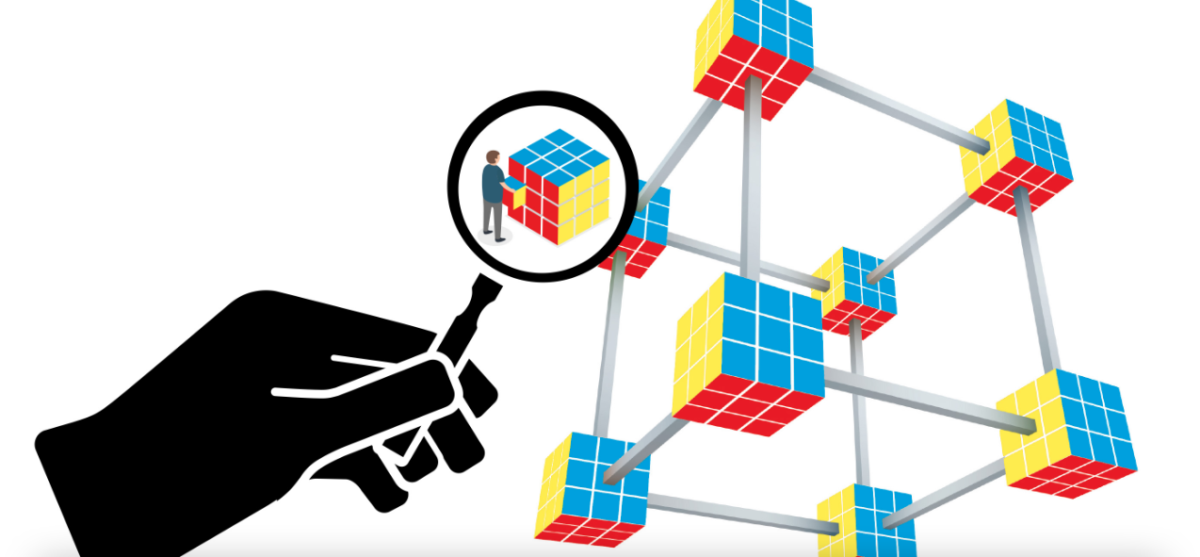
The Internet is an information network, through which data travels, but it did not seem made to carry out commercial transactions, contracts, financial operations. Blockchain proposes collaboration and security to be able to do it.
Two people make a document with an agreement and put it in a glass box, closing each one with a padlock. One hundred people are looking at the ballot box and receive a copy of the agreement. They ask a third person to join the agreement, open both padlocks, this person adds something, gives copies to 110 people who continue to look at the ballot box and puts a third padlock. For a fourth to join, all three locks must be opened and more people will watch and receive copies. Everyone can read the document, and when the locks are opened you can read and add something, but not change what is already agreed.
The document is only one, but every time someone signs it, there are more padlocks and there are multiple witnesses. Each operation causes the document to be protected by more locks. And in the unlikely event that someone did manage to open them, there would be too many witnesses to say that person was not authorized to sign the document.
That is the principle of blockchain (“chain of blocks”, each operation is a block), a technology that seeks, using cryptography and collaboration, that there is more security in operations between people. .
cryptocurrency
Bitcoin is the best known example of a blockchain. It is a cryptocurrency (money based on the principles of collaboration and cryptography) that has been growing in such a way that it has made governments think about the way in which transactions made in this way can be regulated.
Bitcoin users are already millions in the world and thousands of operations are made a day , which leads to millions of padlocks that make it practically invulnerable: it is not possible for anyone to appropriate anyone’s bitcoins if there is no Approved transaction.
But it is only one of several existing cryptocurrencies. And cryptocurrency is one use of many that blockchain has.
Business operations using blockchain
Under a blockchain system, cryptocurrencies, electricity, working hours, and almost anything can be traded, explains Joaquín López, from Kolokium. In addition, businesses that require the fulfillment of several conditions to be carried out can be insured. In these cases there is talk of Smart Contracts.

The Spanish company Kolokium, an ally of Cadena, is one of the pioneering Spanish-speaking companies in traceability solutions through Blockchain, thanks to its Truetrace system that allows any object to be identified, located and tracked in an unalterable, public and permanent in time.
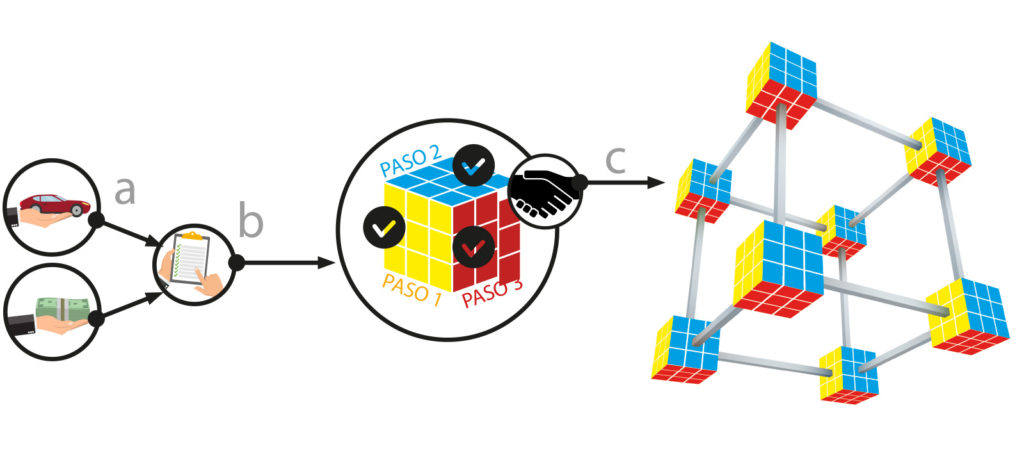
Each movement is registered and stored in the Blockchain as if it were an accounting book.
decentralized custody
Blockchain is a decentralized system: the information is not found in a single deposit, it is in thousands of servers (miners) connected to each other. In each of them, the file is updated with each new block, that is, when an operation is performed.
This makes it work as an endless database and at the same time as a backup copy that is replicated countless times. The fact that the data generated during a transaction is recorded in several servers ensures that it is safe, in case one of the nodes fails or disappears.
The need for a trusted third party in the physical world that endorses and certifies each transaction disappears in the digital world with Blockchain.
Trust
In the physical world, institutions have been created that function as third parties that certify data, transactions, identities, etc. In these systems, what gives confidence is the centralization of information: the parties depend on an entity that is the one that accredits or certifies that what they say is correct. In general, this information is not shared except at the request of the parties.
Public access to documents proposed by the blockchain facilitates certification based on the file itself. So that the chain is not broken, the nodes must validate each transaction, and in the event that one detects an irregularity, the process is suspended.
Validation
Transactions are considered concluded when all the steps of the process have been validated or rejected by the actors involved.
The miners: they can indicate if there are fraudulent actions or a step is being taken without satisfying a previous condition.
The parties: the contract is approved when all the steps of the agreement have been made effective. Otherwise, it is not made effective and each person retains its properties.
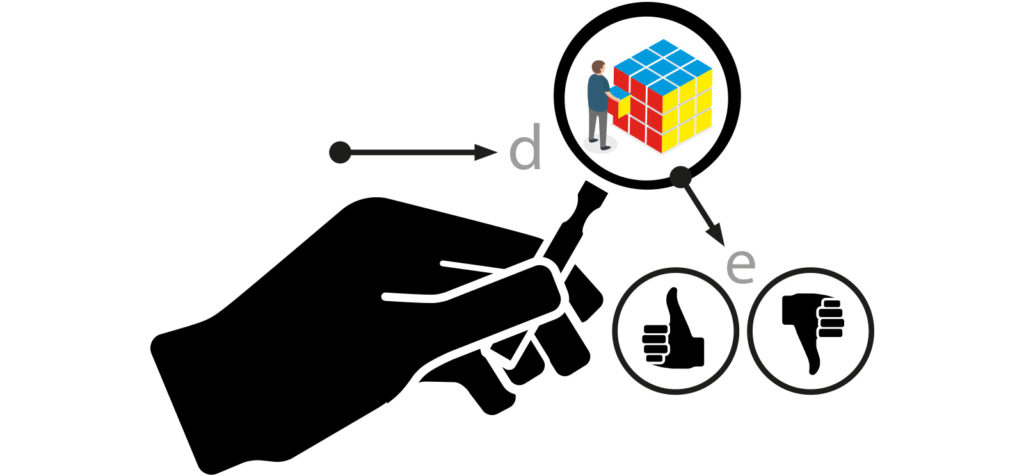
The next step of the contract is not continued until all parties have reviewed and approved it.
Diplomas and resumes
The falsification of the documents that certify the knowledge acquired or the abilities of a person is increasingly common. Through Blockchain, it is possible to set up a whole secure, participatory and easily consultable public structure, through which each institution writes in the registry book, what knowledge or skill it is certifying. The physical diploma or letters or communications are not required, which will always be susceptible to falsifying or adulterating. Likewise, each employer can add to the record the experience of its employees, in such a way that a very complete and true resume of each employee is obtained at the end.
Appellation of origin systems
Health systems, education, banking, registration of real estate operations… the system can be implemented in all sectors. For products that require traceability, for example those with a designation of origin, programs can be created that allow seeing the original product, the actors that have intervened in the chain and the point at which it is each time.
property registration
The characteristics of the Blockchain and its Smart Contracts applications make this technology have an obvious application in the ecosystem of buying and selling properties. The specific conditions of each sale are established, each part of the transaction is authenticated, the specifications of the property or property being negotiated are verified, compliance with the specific characteristics of the contract is verified, and the property title is changed. In this way, the inviolability of property records and the constant updating of the cadastral system are guaranteed. Each record is necessary to make the next transaction of a property.
This system can be connected with the cadastre and with the DIAN, to guarantee that the procedure complies with the law.
Related questions
Because it is:
- Immutable: the information is permanently recorded as it was recorded. Does not allow changes to the above.
- Open: Integrates systems, applications and people working together.
- Secure: a new block can only be created by someone who is authorized.
- Trusted: Each transaction has multiple validators plus it is encrypted.
- Simple: the interested party can consult the transactions in real time, saving time and resources.
Not necessarily. Blockchain is a system that allows different rules to be defined: some elements of the blocks can be visible and others can be codified. That way, the miners can verify the block, but only the parties see what is being traded. Or a party may see that its counterparty meets conditions, but not know who the counterparty is.
“That question is equivalent to asking ourselves in which sectors the Internet had the most potential, the answer to which would be that in all of them. Due to the characteristics of blockchain technology, it is especially appropriate for sectors/projects characterized by the use of common databases, which have to be accessed by various entities that do not trust each other and therefore require some mechanism that generates trust. From here, sectors can obviously be established whose adoption will be faster due to their potential to save costs and generate trust, as is already happening in banking, utilities, medicine and insurance, which are the fastest adopters of this technology. But it will extend to the rest, we have no doubts about that aspect”.
Joaquín López Lérida, kolokium